Of all you need to do is unblock 'Security blocked' files, just use 'streams' (copy the 32 / 64 bit 'streams' .exe along with the appropriate .cmd file from my zip set to the 'root' of the folder (or mapped drive) containing the 'blocked' files and click on 'unblock-all.cmd'.
Why can't I delete a file ?
So you have identified a virus / root-kit / ad-spam file and clicked 'delete' only for Windows to refuse to delete it - or, perhaps worse, it deletes 'OK' only to reappear a few seconds later !
If you are lucky, Windows give you an 'unable to delete file' response - if not, Windows 'locks up' and the only 'cure' is a hard reset (pull the power plug) Sometime you will get a message like 'This file is protected' or 'You do not have permission' More often you will get 'The File in use by another application' (with the usual 'Microsoft help' (i.e. useless) tip 'close the other application'). Very occasionally you might be informed that 'The File Name is too long' .. The 'file name' includes the path, and the max. length of path/name in 32bit XP is 256 characters. To delete a 'name too long' file, you can 'step' to the folder from a Command Prompt window (and then use 'del' command) or use 'map drive' to 'map' the folder that contains the 'too long' file (which then 'shorts circuits' the path to a drive letter)
Protected (Read only) and 'insufficient permission' files
Normally, when you try to delete a 'read only' file you just get an 'are you sure ?' (to which you can reply 'OK'). However this assumes 'you' (i.e. the User Account you are logged in with) has 'permission' to delete that 'read only' file.
The easiest 'fix' is to log-in as Administrator .. and, if necessary 'take ownership' of the file (via Properties, Security tab)
Sometimes even the Administrator is unable to 'take ownership' - these files are 'owned' by the 'system'
In general, however, you can always 'delete' files from a CMD window no matter who the 'owner' is (although you might have to reboot into 'safe mode' to do so)
File 'in use'
When you are in the process of 'editing' a file, the application (MS Word, Paintshop Pro etc) places a 'lock' on the file to prevent other applications making changes at the same time.
Unfortunately, if the app. crashes during the edit, the file can be left in a 'locked' state. Some apps. (such as PaintShop Pro) will hold a file 'locked' even after you finish the edit (i.e. even after you save and close the file), and will only actually 'release' the file when the app. itself is closed. Finally, for some obscure reason, Windows explorer will often 'lock' files even when there seems no logical reason why it should do so (this seems to occur more often on files that you copy to/from a 'mapped network' drive) Indeed, 9 times out of ten it's explorer that's holding the file (despite the fact that you are using explorer to perform the 'delete' !)
Needless to say, Windows provides no way to discover which application (if any) is holding the file 'locked', and no way to 'unblock' a file (although a reboot will often do the trick)
Fortunately, there are a number of 3rd party apps. that can both reveal which app. has the file locked and also 'unlock' the file (no matter what the app.). The best add an option to the 'right click' menu I use 'Unlocker 1.9.0', which also has the added capability of deleting the file on the next reboot (using a DOS 'command' before explorer.exe starts up and prevents it)
The re-appearing file
It didn't take the average hacker/virus writer (and 'commercial' software vendor) too long to work out how to prevent you deleting their virus / root kit / advertising 'server' or 'phone home for an update' garbage. The trick is to infect your system with a file that would be launched at start-up as a 'service' (usually via Microsoft's gift to hackers, the svchost.exe 'front end' wrapper). This service then loaded itself and other 'protected' files into RAM. It would then periodically check for the existence of itself and the other 'un-deletable' files on your hard disk. So when you deleted it or any of the other files from the hard drive it would recreate them from the copy held in RAM
Usually, booting into 'safe mode' would stop the 'service' file from launching at start-up and thus allow you to delete it
Their next trick was to infect you system with two (or more) files that ran at start-up and 'monitored' the existence of all the other files ! Thus, when you succesfully deleted one of the 'servoce' files, it would be immediately recreated by one of the others !
Again, booting into safe mode 'worked' - but only if you managed to find them all and delete them all !
Some commercial software (Adobe) also use the 'service to monitor the files' approach (indeed, most Adobe applications will even recreate the 'Adobe Update Service' and set it to run automatically at start-up (i.e. just like any other unwanted spam))
Security 'blocked'
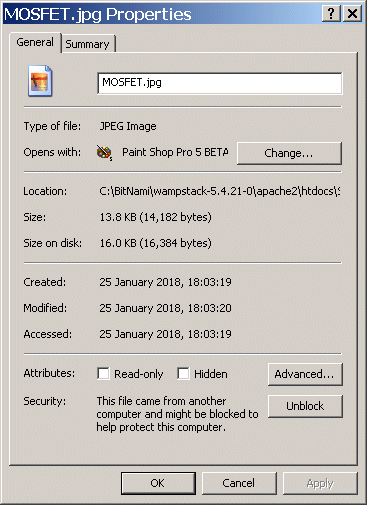
In about 2012, Microsoft started to 'play' with 'hidden' attributes in the NTFS filing system (in yet another half-hearted attempt to make MSIE 'more secure'). The 'concept' of 'marking' files 'sourced' from 'foreign systems' (i.e. those downloaded from the Internet) as 'unsafe' was good (better would have been to tear out all Windows 'auto-run' crap). However, in practice, this just resulted in files that could be copied just fine - but then couldn't be renamed or 'deleted' - and led to system freeze (that required a hard-reset) !!
Yes, it was yet another gift to the hackers and virus writers, who were only too happy to 'mark' their more visible unwanted files as 'blocked' !!
The only way to discover a 'blocked' file/folder is to 'Right click' and open it's 'Properties' window. In the space below 'Attributes' you may find a new entry marked 'Security:' (only XP admin group users can see this = others ware just left to wonder why their computer keeps 'locking up'). You are informed that 'This file came from another computer and might be blocked ..' (== the file 'might' be blocked ? does that suggest that even Microsoft has no idea what effect the 'Security attribute' has ??). If you click the 'Unblock' button the 'Security:' entry goes away and the file can now be deleted/renamed just fine - and all seems fine until you discover all the other files in that folder are 'blocked' !
Yep - the 'Security' setting is an 'attribute' that can be assigned to a folder and thus 'inherited' by everything placed in that folder. Since, by default, 'attributes' are indeed 'inherited', the 'blocked file' tag is 'propagated' down the folder 'tree', thus 'infecting' every other file added to that path (this also applies to Zipped files - if the 'container.zup' is marked as 'Blocked', you will be able to unzip the contents, but ALL THE UNZIPPED FILES WILL BE MARKED AS BLOCKED !!!! Since Windows provides no way to 'search' for 'blocked' files the only way to 'detect' one is to open it's Properties. Worse, blocked files can then only be 'unblocked' (via their Properties) one at a time (which makes for some good fun after you just moved 10,000 photos into a folder infected with the 'Security blocked' attribute !
From MS point of view, adding the 'blocked' attribute also has the 'advantage' of trashing most, if not all, 3rd party file copy and backup utilities, which would typically lock up or crash when they tried to copy files with the 'blocked' attribute
How files become Blocked
When an application (Web-Browser, E-mail client, etc.) saves a downloaded file on a disk formatted with NTFS, a flag can be set to indicate where the file came from (i.e. the 'zone' = Trusted / Internet etc.). The flag is in the Alternate Data Stream (ADS) bits of the NTFS filename.
When opening a file with ADS flags that indicates it is from the Internet zone, the Attachment Execution Services (AES) service is activated. This recognizes 3 categories of files:-
High Risk - Will block the file from being opened, when the file is from the restricted-zone:
Windows Security Warning: Windows found that this file is potentially harmful. To help protect your computer, Windows has blocked access to this file.
Moderate Risk - Will prompt with a warning, before the file is opened, when the file is from the internet-zone:
Open File - Security Warning: The publisher could not be verified. Are you sure you want to run this software?
Low Risk - Will open the file with no nags
Then, in about 2013, Microsoft released a 'security patch' that 'enforced' the 'Blocked' file flag in such a way that attempts to delete the file would result in 3rd p[arty applications locking up is such a way that the only way to 'terminate' the application was via a hard power-off reset.
Why does this have such an impact on 3rd party back-up apps. and not MS 'explorer' ?
Well, unlike 'explorer', almost all 3rd party back-up software adopts a 'safe' file copy procedure i.e. they first copy the source file as a '.tmp' version onto the destination drive, and then, only after the copy has been safely verified do they rename the .tmp to the correct name. This ensures that, for example, if a file of the same name already exists at the destination, it is not 'overwritten' until a 'good copy' completes. Needless to say, 'blocked' files would copy (to .tmp) just fine - but could not then be 'renamed' - thus causing the utility to lock-up or abort. So, if (when) your 'Free File Sync' (or other file back-up utility) freezes, forcing you to power-cycle your PC (and then search for and delete all '*.ffs*' files), you can blame Microsoft for yet another half-implemented P.O.S.
The 'cure' is to use the sysinternals 'streams.exe' (or 'streams64.exe') utility from the CMD line (from within the folder containing the 'blocked' files)
streams.exe -s -d *.*
Using Streams in this way removes all the 'hidden' attributes, including the 'blocked' bit
How to prevent files being marked as Security 'blocked'
DO NOT just add all file socurces to yout 'Trusted Zone' - whilst this will work, it will, in effect, disable your anti-virius and firewall functions !
For files on 'shares' on trusted machines on your LAN :- Add the network drive, IP-address or the UNC to the list of sites for the "Local Intranet"-zone MSIE will need to uncheck the "Automatically detect intranet network" option first If the file-type is not considered dangerous (ex. mp3), then you can add the file-extension to the list of "LowRiskFileTypes"
To disable the stupid marking of downloaded files as 'security blocked', set the Registry Key :-
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments\SaveZoneInformation = 1.
In theory this should work for all (newly) downloaded files ... for me it didn't. For more modern versions of Windwos (i.e. after X), an alternative is to use gpedit :-
Disable the Atttachment Manager
This should prevent any new files being 'marked' as blocked. Run the 'Group Policy Object Editor' (gpedit.msc) either from the Command Prompt or using the 'Run' command in the Windows Start Menu. Then :-
Expand the node 'User Configuration' >> 'Administrative Templates' >> 'Windows Components' >> 'Attachment Manager'. Right-click on the "Do not preserve zone information in file attachments". Choose 'Properties'. Select 'Enabled' (Enabled means that 'Do not preserve zone information in file attachments' is enabled, which will stop Windows from storing the zone information in file attachments). Click Apply, then OK to close the dialog box.
This comes into effect on the next reboot (or you can run the command gpupdate /force
Note. Users of MS Office 2016 (Word and Excel) should go to File, Options, Trust Center and 'untick' all 3 of the "Protected View" tickboxes.
configure the Attachment Manager via the Registry
The Attachment Manager can also be configured via regedit:-
Find the Keys in User Configuration, Administrative Templates, Windows Components, Attachment Manager. The key "Default risk level for file attachments" controls how to treat files that are zone-marked and not found in the built-in lists of known filetypes. By default it treats unknown file as "Moderate Risk". [HKEY_CURRENT_USER \Software \Microsoft \Windows \CurrentVersion \Policies \Associations] DefaultFileTypeRisk = 6151 (High = 6150, Moderate = 6151, Low = 6152) The key "Do not preserve zone information in file attachments" controls whether the Attachment Manager should zone-mark files downloaded from the Internet. By default zone-marking is enabled. [HKEY_CURRENT_USER \Software \Microsoft \Windows \CurrentVersion \Policies \Attachments] SaveZoneInformation = 1 (On = 1, Off = 2) The key "Inclusion list for low, moderate, and high risk file types" allows one to extend the built-in lists of known filetypes and override their default security category. By default the custom inclusion lists are not configured: [HKEY_CURRENT_USER \Software \Microsoft \Windows \CurrentVersion \Policies \Associations] HighRiskFileTypes = "" ModRiskFileTypes = "" LowRiskFileTypes = ".mp3 .wma .jpg" The key "Trust logic for file attachments" sets how certain trusted file handlers like Notepad act when a Moderate Risk file is opened. Eg. with Notepad, then it is considered Low Risk. It possible to configure whether it should take the file handlers into consideration. By default it trusts the file handler: [HKEY_CURRENT_USER \Software \Microsoft \Windows \CurrentVersion \Policies \Attachments] UseTrustedHandlers = 2 (Filetype = 1, Handler = 2, Both = 3) To Disable the checking of zone-markings completely, set the environment variable: [HKEY_CURRENT_USER \Environment] SEE_MASK_NOZONECHECKS = "1"